Bring war material with you from home, but forage on the enemy. Thus the army will have food enough for its needs.
Before the days of ration packs and advanced logistics armies would bring the tools with them that they needed to wage war, but they would supplement their consumables with what they could seize during the campaign.
This is surprisingly relevant to cyber operations.
From a macro perspective, cyberspace and cyber operations are new. New in the sense that we’ve been doing it for much less time than we’ve spent banging swords together, or shooting each other with projectiles. Just like when the sword and bow was first invented, cyberspace has quickly become a conflict zone. In a very real way cyberspace is like the conflict environment just after Sun Tzu’s death, the late Zhou Dynasty. Land and resources were divided completely by military power and mercenaries, armies, and criminals pillaged what they wanted regularly. Like any ancient warring period, today we see criminal gangs taking what they want using disruption, ransomware, theft, and infiltration. We see proxy wars fought by states using mercenary cyber criminal groups. We see states conduct long term and wide reaching quiet offensives. This blog post isn’t about any of that.
I’m going to talk about a concept called ‘living off the land’.
Attackers will certainly “bring war material with you (sic) from home”. They will attempt to bring in custom or prepackaged malware in form of remote access tools, credential grabbers, reverse proxies, web shells, you name it. The arsenal of tools at the attackers disposal relates only to their expertise in acquiring or creating, deploying and welding them. As a defender it is easy to get tunnel vision and fall into the trap of focusing only on combating these toolsets. This is particularly a problem for IT service delivery organisations. As a defender it is vitally important to have a complete understanding of every aspect of your defended environment. If you understand your environment you can analyse an attachers ability to live off the land (or “forage on the enemy”).
Living off the land
Living off the land is a particular style of offensive operations where the attacker uses only what is available to them in the target environment. A lot of good attackers will use a hybrid approach where initial access, maintaining persistence, and C2 is all achieved using exploits and malware, but then lateral movement, defence evasion, internal reconnaissance, and extraction is conducted by living off the land.
Some excellent, and intermediate attacks use only the environment itself in their compromise. These end to end living off the land attacks usually leverage stolen credentials or weak credentials for initial access. Once they are in with whatever level of access they stole (or guessed) they will use what they find on that user machine to start recon and internal movement. I’ll use this fictional hack as a means to illustrate how useful and simple living off the land can be. Let’s flesh out the example.
Situation
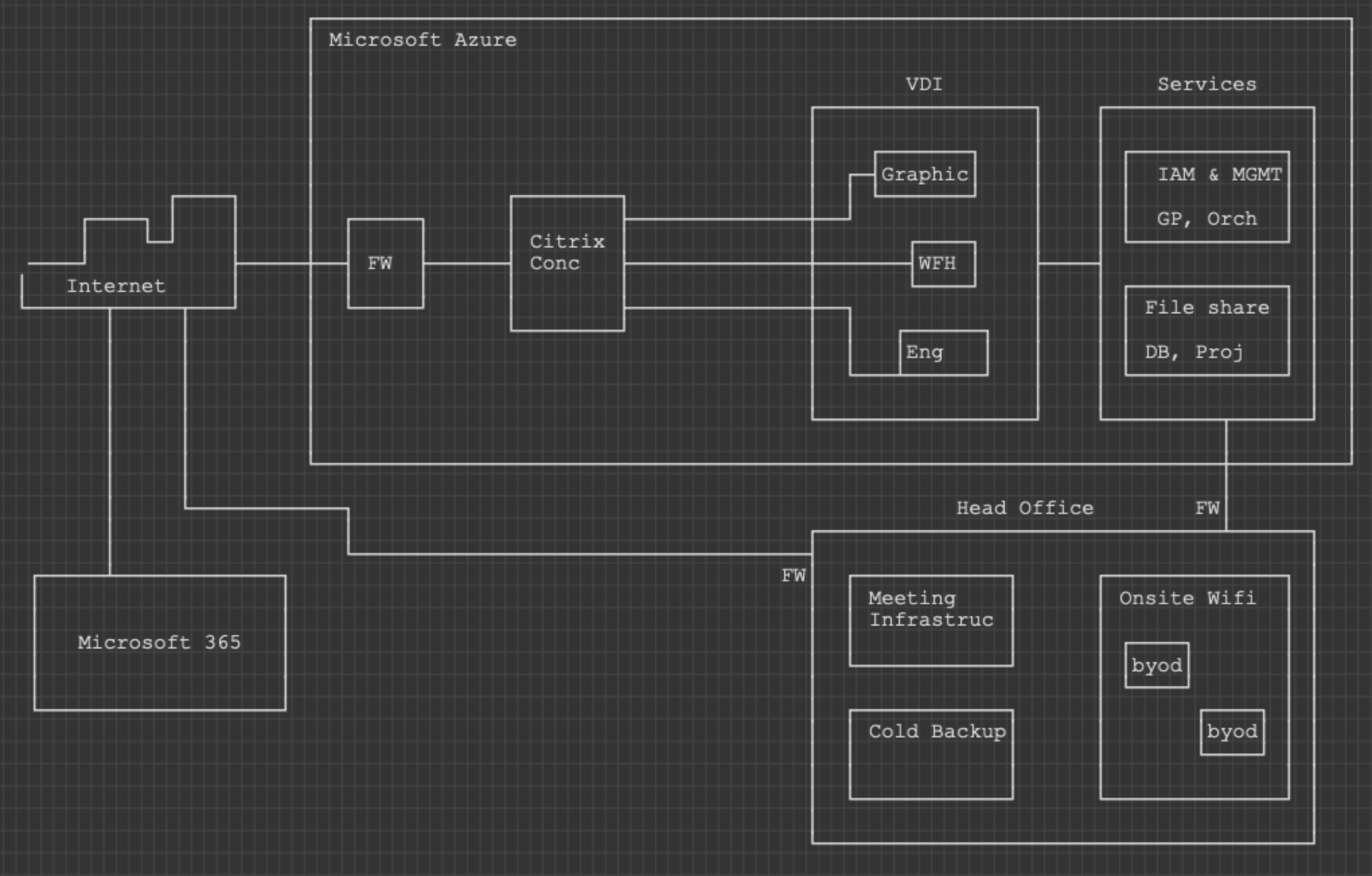
Australian architecture, planning, and engineering company BuildyMcBuildFace was initially hit hard by the great pandemic of 2020. Fortunately they have a good IT service delivery company on the books, and are forward thinking business people. They have reduced their physical footprint from three whole floor offices to one office with a large technology investment in working from home. This has proved to be a resilient working model and they will continue it even if the pandemic disappears tomorrow (one can hope). To facilitate this their IT service delivery partner has created an environment that transfers everything to operating costs and reduces capital investment in IT infrastructure. It leverages cloud computing, byod, SaaS, virtual desktop infrastructure. The works. Heres what it would look like… sort of.
Pretty cool huh. It works like this: a user can be at home and log in through the citrix concentrator with their Azure AD creds. When they do their desktop gets spun up in the virtual desktop infrastructure pool (VDI). From there they have access to the file share, databases, and the programs they need to complete work for the business. The head office also has an internet connection so they can use the Citrix entry to the VDI and Microsoft 365. Because the organisation has elected for a BYOD approach they give employees an allowance toward buying a personal device for use in the work environment. When they connect to the VDI the concentrator does some light health checking of the BYOD device, but doesn’t look for full security compliance. There is also an IPsec tunnel into the back end of the Azure environment which allows AD to be used for the wifi authentication, and allows local admins to administer the system. There are also cold backups of Azure images in the head office which transfer monthly from the hot backups kept in Azure. Lastly there’s a small amount of meeting infrastructure (such as Teams tablets and video conferencing gear) which is networked through the head office.
This on-demand compute for users and access anywhere environment allows BuildyMcBuildface to have 300 employees but only a 450sqm office. This environment also allows some pretty cool defensive security controls. The crux of the security model in this environment is built around VDI. The VDI is set to destroy the users virtual machine when they log out. You heard me, the user machine is DESTROYED. Then a new instance is orchestrated at login. Sure, it takes an extra 3-5 minutes a day to log in, but the pay off is big. How would an attacker maintain persistence on a computer that is destroyed every day? How can an attacker use malware running in memory to evade file system scanners? How can an attacker be assured they will maintain C2 if the remote access tool is on a filesystem that is destroyed every day? The short answer is they can’t. The long answer is they will live off the land.
The Threat Actor
BuildyMcBuildface is the front runner in negotiations to design and build a huge international sports campus (including a national stadium) for a pacific nation. It’s a pretty sweet deal. There are two other candidates, but it looks like BuildyMcBuildface is going to beat them to the contract through excellent negotiations, reputation, and value.
A criminal group, who is classified as an APT (Advanced Persistent Threat) operates in the ‘near pacific region’ under the name “L33t H@x 4 hire”. Six weeks before the contract negotiations close on the sports campus L33t H@x 4 hire gets a new assignment. A party they have worked with before has private messaged them on one of their Darknet Forum pages. They give an address for an escrow Monero wallet which holds $250,000 US in Monero, along with the message:
(feel free to read this in an ominous digitally distorted deep male voice)
“Your target is BuildyMcBuildface. We require them to be taken out of negotiations for the pacific sports campus deal. You have three weeks to destroy all data relating to the sports campus deal and ruin their reputation. The usual fee is being held and will be released when BuildyMcBuildface has been eliminated from the contract.”
Wow what a shady deal. I won’t even postulate on who in the near pacific region would want to destroy an infrastructure deal, and this is definitely just a fictional example anyway. L33t H@x 4 hire take the job.
L33t H@x 4 hire do their reconnaissance. Almost immediately they find that the IT service provider has used the BuildyMcBuildface network as a reference architecture for how great they are at delivering VDI and BYOD solutions. Included on the company website is a blog entitled ‘IT Service NOW not tomorrow or the day after’. In a blog post the cloud engineer has included a shitty ASCII art diagram of the environment.
Now L33t H@x has found out about the VDI security controls. They realise can’t just drop a remote access tool on a VDI machine. They’ll have to live off the land.
The Hack
The new task for L33t H@x gets assigned to one of the hackers in the organisation. They asked HR for a more challenging task so their project manager has allocated them this no-malware hack. We’ll call our hacker Man, no Han… Han Solo.
Han Solo completes their initial reconnaissance by enumerating the email addresses associated with BuildyMcBuildface. This gives them a number of usernames, addresses, and names of people to gather intel on. Han Solo has a couple of considerations when choosing a target user: pattern of life, personal cyber hygiene, and digital footprint. Our hacker chooses a couple of targets, and after an initial automated examination a promising target user is selected: Enrico O’Connor. (can you tell I used a name generator. My imagination is getting tired)
Han Solo works the open source intelligence for Enrico. He compiles a dossier of information he can quickly collect about Enrico.
Corporate Profile: Graphic Designer, Intermediate level, not management, phone number, email - Enrico.oc@buildymcbuildface.com.au, employed for 18 months.
Digital Footprint: Facebook, Instagram, LinkedIn, Adobe, DeviantArt, WhatsApp, Signal, Apple iPhone, Twitch, Discord, Steam, Twitter.
Personal Cyber Hygiene: Facebook is partially open, Instagram is fully open to showcase work and lists a gmail email, LinkedIn is partially open though they accept connections easily, Adobe profile is open to sell stock imaging, DeviantArt is an open profile of somewhat smutty illustrations, WhatsApp he is part of a number of 100+ member open groups, Signal is signal, He twitch streams regularly, he is part of a number of large discord servers and has game integrations turned on, his Twitter posts semi regularly. A quick search of the corporate and gmail address finds that the emails are listed in a number of previous compromises. The gmail email tends to get left around the internet a lot. Enrico also doesn’t seem to care too much about who he connects with on digital platforms.
Pattern of life: using Facebook, discord, WhatsApp, and twitch activity Han Solo determines that Enrico works a modified Australian work day. He wakes up around 10 and starts working shortly after, sometimes as late as 11. This can be found using the seen statuses in the large WhatsApp groups, the active now on Facebook and Facebook messenger, and from the fact that he often live streams his gaming until 1am. He tends to talk about his work generally a couple of times a week on discord in some of the midsize gaming servers. Because his discord is integrated with League of Legends and most of his other regular games Han Solo can tell when he starts playing. Typically he plays heavily toward the end of the week, with some interruption where he seems to work or be out judging from his Facebook activity.
Han Solo runs the gmail and corporate emails, along with some usernames derived from his digital footprint through a number of previously compromised databases, pastebin, darknet databases, and L33t H@x own credential harvesting data warehouse. He gets consistent hits for two passwords which have been reused across seven accounts. The passwords are very similar, indicating a weak personal password cycling process. The reuse combined with password similarity means Han Solo now has Enrico’s password, or something close enough to it.
Han Solo knows that the Azure AD environment is set to allow concurrent logins, because it is used across platforms and protocols (VDI, Wifi, Microsoft 365). He doesn’t know if the VDI will allow concurrent logins, or if a concurrent VDI login will alert. So Han must assume that logging in concurrently with Enrico is off the table. Using the pattern of life analysis Han Solo determines that the times he can access the VDI with a higher level of stealth and assurance of access is 0800-1000 AEST Mon-Fri and in the evenings in the middle of the week. Han Solo can determine when to log in in the evenings by setting an alert on Enrico’s discord or twitch activity for when he loads a game. As long as he confines his evening logins to be out before 2200 it should be less noticeable in logging.
Han Solo chooses his time windows to begin. He starts his VPN, loads up his anonymous VPS, and starts his process.
I’m going to lay out all the technical parts in one go now and jump to the end of the hack. The learning is in the moral of the story, not the journey.. or something, maybe it is the journey, but sped up. Here look at this diagram:
Sweet hacks.
Han Solo uses pre-harvested credentials to log into the Citrix concentrator and spawns a Graphic Design VM. The VM has a number of graphic design applications and some access to the Microsoft Project server as a resource, and some access to the graphic design and marketing folders on the file share server. The VM also has basic Windows Enterprise tools still enabled by default. The attacker loads MMC and find he has read access to the AD domain and group policy. He does his recon and established the IAM structure, groups, roles, and accesses. He looks through the group policy and finds that the windows domain logging is set to default. This indicates that it’s unlikely the user VM’s logs are collected and alerted on in any way. The Azure AD may be another matter. Theres a distinct lack of group policy configured beyond default on the user machines. The admins must think destroying the machine daily delivered enough security. There is application whitelisting implemented, but with such a short VM lifetime Han Solo won’t be using malware anyway.
He finds that PowerShell is enabled and better yet that PowerShell remote administration is enabled. It’s probably there because of some orchestration that’s used to spawn and configure the VDI platforms. He uses PowerShell to do some network recon. It seems as if all of the user hosts are on one flat virtual subnet. He can see that there is a link to a management and services subnet next to the VDI subnet. His graphic design user is unlikely to have access to any of the services or management virtual machines, but if he can find another credential he may be able to move there. From the functional naming scheme he can tell what type of user will be on what VM. It looks as if there are some engineering VM’s spawned. It is likely that if his machine has PoweShell remote administration enabled then the others will as well. From the domain group structure it also looks like all of the VDI users are in one group, as well as their sub-groups. This indicates it’s likely he’ll have access to an engineering machine, just not the ability to spawn one on login.
Sure enough Han Solo is able to use PowerShell to remotely run commands on the engineering machine. He still only has user level access, but he has a different kind of machine. He pokes around using PowerShell remote administration and finds that the engineering VM’s have a number of technical and structural drawing applications installed.
The CAD application itself isn’t helpful however there is another application which looks like it connects to a database in the services subnet. A quick google of the application reveals that it is a plugin for the CAD application which searches an MS SQL database for engineering objects (e.g. a specific size of steel beam which can be easily ordered etc.), why draw the materials and parts of a building from scratch when the manufacturer provides the drawing to encourage ordering. The application contains two binary executables and a number of configuration files. One of the binaries is an SQL client interface, useful. The other is the main executable. The configuration files contain, well… configuration. Specifically configuration which allows interface with the SQL server, including (drum roll) credentials :).
The CAD application has been set up to use a read-only admin type user to interface with the MS SQL in the services segment. Han Solo uses the SQL tool binary and the credentials he found in the config files to run some SQL commands against the server. It works. They are truly read only though, and the database does not contain anything of value. It does however tell him that he can get from this machine into the services segment, and that the credentials work.
He cross references the credentials with the map of AD he was able to make earlier. It looks like even though this user is read only for AD and SQL it is still in the admins OU folder. He can also see that the user is not nearly as old as most of the other admin accounts. This indicates that the CAD item database and application were set up a while after the rest of the environment, which explains the unique nature of the account. One of the hostnames in AD seems to be for a management VM. Using the admin read only credentials Han Solo makes a connection from the engineering VM PowerShell to the management VM. Now that they’re in the management VM is time to take a peek at where the admins hang out. Han finds a number of administration binaries, some scripts, a load of Powershell modules already installed, and some documents. The most useful of these is the admin binaries and the PowerShell modules. Most of the Azure Powershell modules are installed, including the Azure Automation and Azure AD modules.
One of the binaries is a password reset binary that seems to be part of a password self service application. Han Solo runs the binary in the PowerShell session and finds that it wants input of a username, it looks like it was made by an admin and not a purchased commercial product. Han Solo resets the password for one of the Domain Admin users which has an expired password (must have moved on, or been assigned to a different customer). He them promptly disables all the other admin accounts using his new access in Azure PowerShell. That may have raised flags soon if anyone is watching but he’ll be moving pretty fast now and it’ll buy him a lot of time. Han Solo pastes in a quick PowerShell script which will disable then delete every user in the domain, he sets it to run after initial execution in 10 minutes.
Using his new admin access Han Solo examines Azure Automation. There are a number of playbooks. He finds one which takes a backup of all the information in the file share server, the project server, and some Sharepoint information from Microsoft 365. This is going to be the information he wants. Now he knows where all the information he wants is neatly packaged up he can get it out and burn everything else to the ground. Han Solo makes another script, this time to detach all the virtual disks in the file share server, the project server, and the management server, and then delete them. He sets this script to run 30 minutes after execution. He looks and finds that the last backup was 2 days ago. Thats plenty recent enough. He examines the backup playbook, it backs up to a linux server over an SSH tunnel. The SSH key is stored in an unsecured variable in the playbook.
Han Solo makes an SSH connection to the backup server in the head office. It’s an Ubuntu 18.04 server, with a striped RAID 5 array.
He checks the file share server again and decides execute the backup playbook again in ‘diff’ mode. This copies all the files that have been updated or modified in the last two days down to the backup server. This takes about an hour.
The firewall that services the head office internet connection allows all outbound protocols to establish. Han establishes an SSH tunnel out and starts moving the most recent complete backup to his VPS, along with the diff files. Once he is done Han Solo sets a script to wipe the mounted raid drive repeatedly, infinitely (presumably until someone physically turns off the server), he wipes all of the Azure AD logs, all of the Automation logs, and then he then executes his two destruction scripts, and logs out.
L33t H@x 4 hire destroy BuildyMcBuildface’s data and denied them their network a week before the critical point in their negotiations. This prevented them from being able to deliver their tender on time. L33t H@x also publicly released a lot of the information stolen that pertained to previous customers. This damaged their reputation and was received poorly by the pacific nation’s government.
What did we learn
Look a lot of readers are probably going to pick apart the hack and say ‘what about this’ or ‘but if they had just done X’. I’ve seen a lot of organisations with different combinations of the insecure implementations used here. This was a hypothetical hack, but still a very possible one.
Defenders and security vendors focus a lot on stopping malware. Shutting down malware is very important, especially in the current Ransomware crisis. However we are losing focus on secure implementation and IT service delivery is losing their grip on their understanding of the systems they administer. As we close the door to malware, another door is left open. In this attack scenario the attacker used no malware whatsoever. All they used was a big ol’ brain.
Even if we leave offensive operations out of it, insider threats, intentional or unintentional can use your environment against you. That finance person who thinks they’re an IT Ninja so they start screwing around in mmc snapins? Why is mmc available to them? What about that woman who just got fired. In the time she has left at the organisation, what could she weaponise?
My advice
Whenever you implement something, turn on a feature or facility, bring a binary or a new service into your system please go through a decent analysis on it. Think about how it could be used against you. Put yourself into the mindset of the attacker. Look for a better way to implement whatever you are doing. Attackers often use a hybrid approach, if they use exploits and malware to blow past a couple of layers of your defence, will they then be able to use your own tools against you?